How to extract email addresses from a text file using notepad+
Given the following text file as input there are 3 easy steps to follow so that you can extract all email addresses contained inside the text.
Text containing email addresses
Text containing email addresses
1st Step – Find email addresses using regex match
Use the find & replace feature of notepad++
Find: (\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+.[A-Za-z]{2,4}\b)
Replace: \r\n$&\r\n
find&replace
this adds and new line before and after each email address.
Email address in new line
Email address in new line
Step 2 – Mark email addresses and bookmark lines
Mark: (\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+.[A-Za-z]{2,4}\b)
have “Bookmark Line” checked.
bookmar-email-line
Step 3 – Remove unmarked lines
Search > Bookmark > Remove Unmarked Lines
Remove unmarked lines in Notepad++
http://www.kniko.net/how-to-extract-email-addresses-from-a-text-file-using-notepad-with-no-coding-at-all/

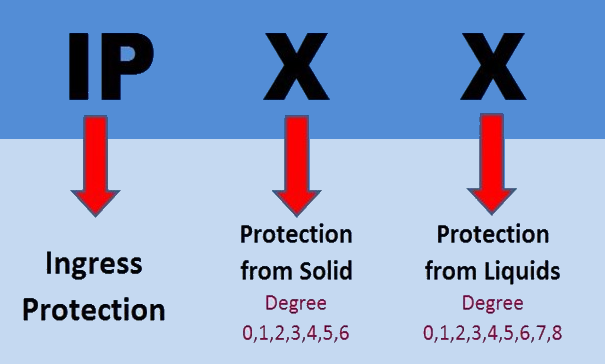

 Home
Home